The IT servers and data centers of enterprises have become the epicenters of cash ransomware threats!
Hackers are well aware that many critical business secrets are concentrated in IT assets, so they have targeted enterprise servers and IT data centers as attack vectors. Can we afford to leave our doors open?
How to achieve real-time detection, enforcement, and correction without sacrificing security or performance?
Today, enterprises are constantly under the shadow of network threats, which are evolving and becoming increasingly sophisticated. Sometimes, these threats are not only more complex than before but are also specifically designed for particular targets, exploiting newly discovered vulnerabilities or attack techniques. Sometimes, they exploit old vulnerabilities that you may have forgotten. Faced with such threats, to protect your data and assets, you need to be aware of the status of all your network layers and resources at all times. Additionally, you need complete, up-to-date cybersecurity intelligence and a dynamic approach to adjust to new threats, vulnerabilities, and changes in the network environment every day.
These ever-changing threats require a multifaceted approach to prevention. It is necessary to deploy comprehensive protection at both the enterprise perimeter and internally to prevent malicious attacks from invading your critical resources. Moreover, complete threat intelligence is needed to guard against known, unknown, and undisclosed vulnerabilities.
Building a robust network protection platform in front of your critical IT assets to provide complete threat protection and precise prevention of known and undisclosed vulnerabilities is an effective defense mechanism.
It can provide advanced threat detection and defense, such as advanced malware, network phishing, etc., with high elasticity and performance. It integrates various traffic inspection technologies, including deep packet inspection, threat reputation evaluation, URL reputation evaluation, advanced malware analysis, etc., to detect and prevent attacks at the network level. It can also provide proactive network protection for enterprises, enabling them to actively monitor the overall network status and conduct in-depth analysis of network traffic. This comprehensive environmental sensing capability, combined with threat intelligence from the digital vaccine lab, allows you to fully understand the security situation and flexibly respond to evolving enterprise network threats.
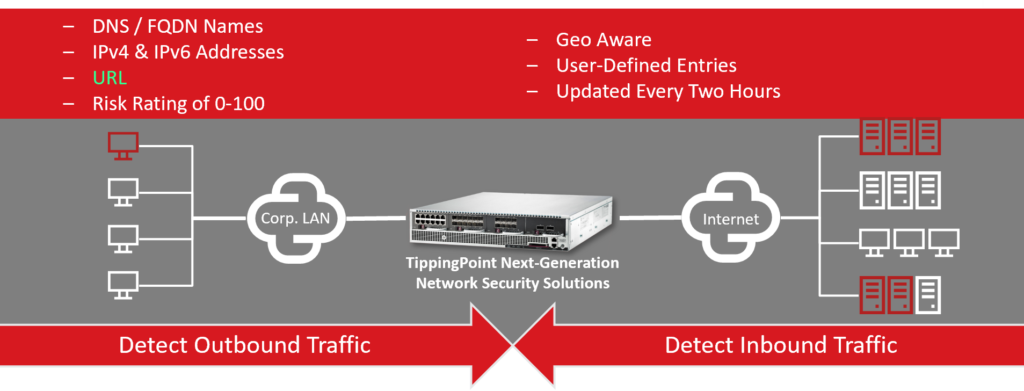
Key Features
Built-in SSL traffic inspection: Many sophisticated targeted attacks use encryption to evade detection. Built-in SSL traffic inspection reduces security blind spots caused by encrypted traffic.
Scalability: As the integration rate of data center systems increases and cloud environments become more prevalent, protective solutions must be able to expand with growing network demands. High-capacity networks provide unparalleled protection and performance.
Flexible licensing model: Easily expand performance and protection requirements with a pay-as-you-go and flexible software licensing model, allowing for reallocation of deployment authorizations without changing the network infrastructure.
Real-time machine learning: Many cybersecurity threats have short lifecycles and are constantly evolving, often rendering traditional detection mechanisms based on feature matching or hashing ineffective. Statistical models developed using machine learning technology can detect and prevent threats in real time.
Advanced threat analysis: By pre-filtering known threats and then submitting suspicious potential threats for automated sandbox simulation analysis, any confirmed malicious content can be immediately corrected.
High availability: It has multiple fault-tolerant features, making it ideal for deployment in-path, including hot-swappable power supplies, continuous monitoring of security and management engine protection timers, built-in traffic bypass, and zero-power high availability. In addition, redundant chaining mode can be used to provide automated Active-Active or Active-Passive high availability (HA).
Integrated advanced threat protection: It can be integrated with Trend Micro’s advanced threat detection solution.
Asymmetric traffic inspection: Asymmetric traffic is a common situation in enterprise and data center networks. Enterprises must overcome the challenge of asymmetric traffic and routing to truly protect their networks. It is preset to inspect all types of traffic, including asymmetric traffic, and applies appropriate protection policies to ensure security.
Flexibility and elasticity: Software-defined network protection is deployed as a service for intrusion prevention. It can also protect your virtualized applications from within your virtual infrastructure (VMware, KVM).
Cutting-edge threat intelligence: The digital vaccine lab provides top-notch threat analysis and protection filtering rules covering the entire vulnerability lifecycle to prevent all potential attack combinations, rather than just specific vulnerability attack techniques, and to prevent undisclosed and zero-day threats.
Virtual patching: Virtual patching provides a powerful, scalable first-line defense mechanism to prevent network attacks from known threats, providing effective protection using vulnerability filtering rules, effectively preventing attacks against specific vulnerabilities at the network level (rather than at the user level). This can help companies control patch update management strategies, provide proactive protection during the window between vulnerability discovery and patch release, and provide additional protection for old, end-of-life software.
Comprehensive support for various traffic: The platform supports a variety of traffic and communication protocols. It provides IPv6/v4 traffic synchronization checks and supports related tunnel protocols. The extensive coverage allows IT and security system administrators to deploy defenses flexibly where necessary.
Centralized management: It provides unified policy and element management through a graphical user interface, centrally monitors all operational information, edits network protection policies, sets up element configurations, and deploys network protection policies across the entire infrastructure, whether physical or virtual.
Key Benefits
Understand threats and prioritize judgments
Understanding threats and intelligence is the key to determining the quality of protection policies. It allows you to fully understand the status of your network and provides the intelligence and environmental information you need to assess the priority of vulnerability threats.
Real-time control and correction
From the perimeter to the data center to the cloud, defend the network by controlling in real-time and automatically correcting systems with vulnerabilities. It provides a new realm of in-path real-time protection, actively protecting today’s and tomorrow’s real-world network traffic and data centers. The architecture can perform high-speed in-path deep packet traffic inspection, while special modular device designs can integrate other protective services.
Streamlined operations
By providing flexible deployment options that can be easily installed and managed from a centralized management interface, it offers immediate and continuous threat protection and factory-recommended settings.
