Comprehensive Endpoint Security Management Solution, Ensuring Complete Endpoint Security
Defense products are also the most serious security vulnerability (blacklist).
Issues with Blacklist Mechanism:
- Constant updates to the blacklist are required to maintain protective capability.
- Attacks not on the blacklist are preset to be allowed and bypassed.
- Unable to prevent attacks by unknown programs.
- Unable to defend against new types of attacks such as Zero-Day, APT, and ransomware attacks.
Which security products use blacklists?
- Antivirus software, intrusion prevention systems, spam email filtering, web content filtering.
ITSM Establishes a New Endpoint Security Management (Access Control) Mechanism:
- Programs not on the whitelist are preset to be denied execution.
- Unknown programs are executed in isolation in a sandbox.
- Hacker-initiated APT and ransomware attack probability is 0%.
Effectiveness of Using ITSM:
Amid the shadow of ransomware attacks such as WannaCry looming globally,
Over 150 countries worldwide were attacked, affecting the normal operations of many financial, medical, transportation, enterprise, and organizational entities.
The good news is,
With over 100 million systems protected under our endpoint security management solution,
We have achieved a record of zero infections again!
This indicates the effectiveness of our defense mechanism!
What is ITSM?
ITSM is a complete endpoint security protection software, integrating various cutting-edge security technologies into a complete endpoint security protection solution, providing comprehensive internal security protection for enterprises and resisting external threats.
How is ITSM Different from Typical Antivirus Software?
Typical antivirus software isolates threats using a blacklist method, while ITSM provides both black and whitelist functions. More importantly, it includes a graylist sandbox management mechanism for unknown programs, achieving complete control and effectively defending against malicious ransomware programs that traditional antivirus software cannot stop.
Three Classification Methods for Effective Defense:
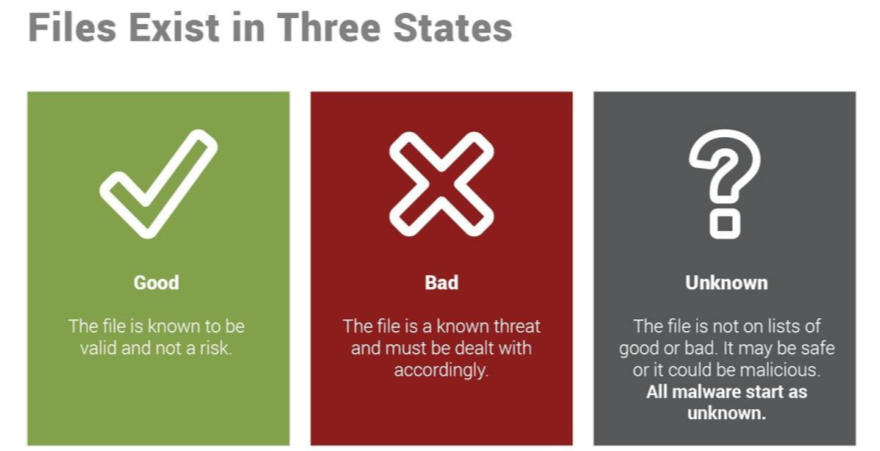
Defense Process for Unknown Files:
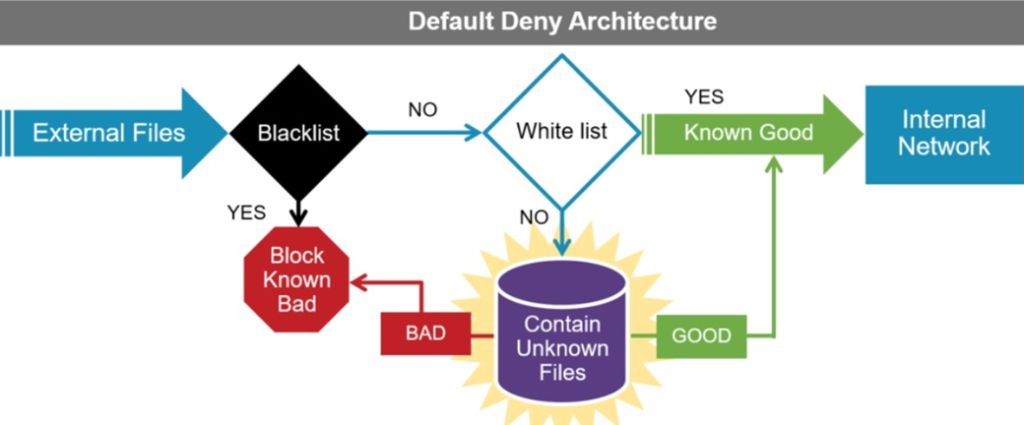
Execution Principle and Defense Process:
1.Identified in the “Known Blacklist,” the program is prohibited from execution.
2.Identified in the “Known Whitelist,” the program is allowed to execute.
3.Considered an “Unknown Program,” it is automatically executed in the endpoint sandbox.
4.No unknown program can access your physical computer devices or network.
5.Automatic local and cloud-based comparison analysis is conducted to determine whether the executed program is a whitelisted program.
6.Execution of programs is permitted or denied based on determination.
7.Does not affect endpoint user experience.
Issues ITSM Can Address:





Functions of ITSM: